Security & Identity Access Management
Services
What about wondering if what your companies spending on security measures are even effective against the bulk of real intrusion issues?
Security Architectures
Protecting your computing environment starts with some often-neglected basics: infrastructure that is securely architected and configured; a realistic, business-oriented view of risk; and focusing your attention on simple measures around the people, processes, and technology you already have in place. Crafted together, what emerges is a plan that will reduce risk to an acceptable level while expending the appropriate level of resources to do so.
In our experience, organizations rarely take an end-to-end view of their security architecture and even more rarely include network and system considerations in the process. Many security consulting companies say “security architecture,” when what they really mean is “more security widgets.” We’ve found that a much more successful approach is to organize the people, processes, and technology you already own more effectively while introducing new security widgets only when the business requirements mandate.
Security Starts Somewhere
You know cyber security is important, but in the absence of regulations, where do you start? We recommend the SANS Top 20 as a great place to begin your security strategy and are ready to help you with implementation. These controls alone can be up to 97% effective against the most common threats your business will face.
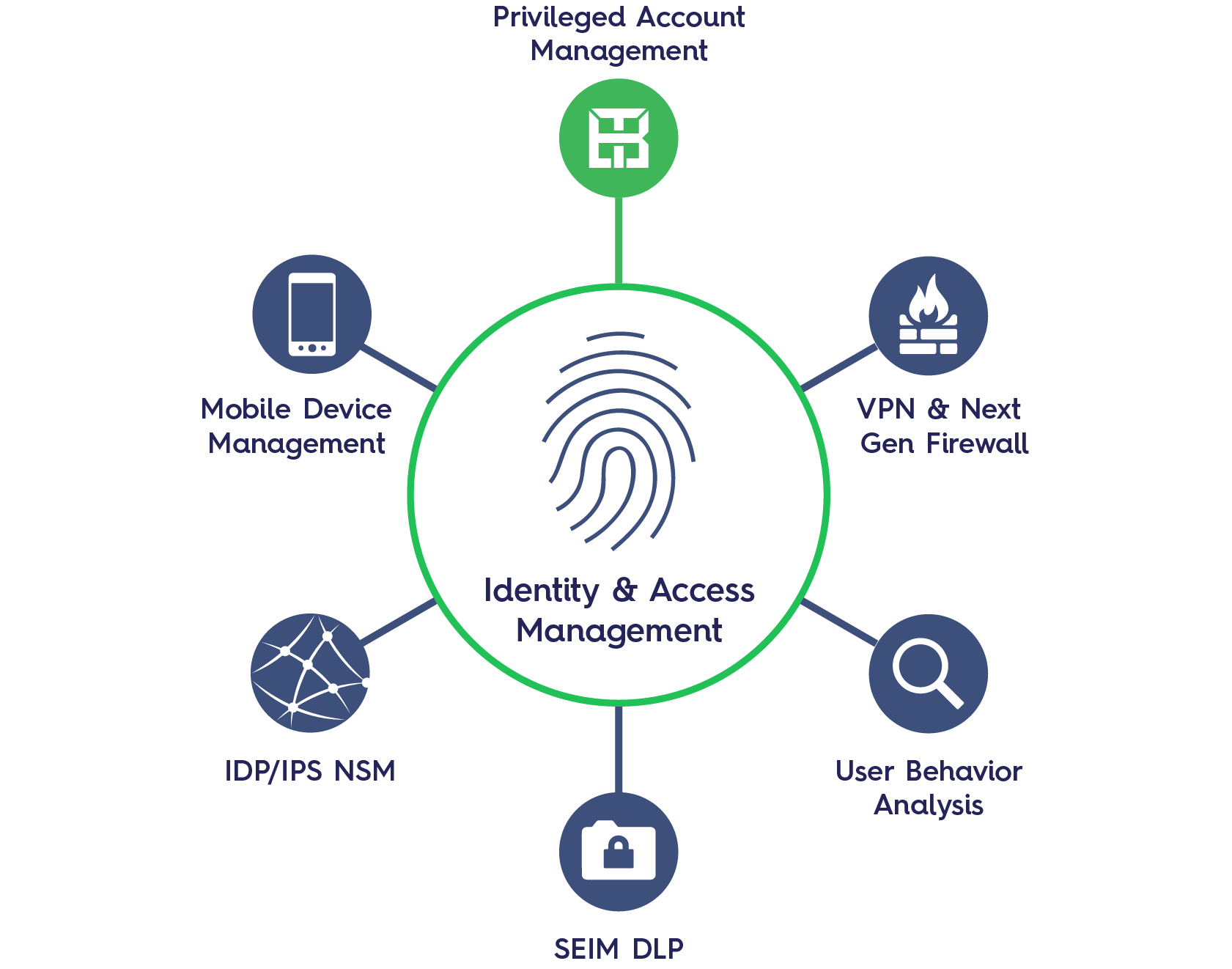
What is IAM?
Identity and access management (IAM) is a framework for business processes that facilitates the management of electronic or digital identities. The framework includes the organizational policies for managing digital identity as well as the technologies needed to support identity management.
With IAM technologies, IT managers can control user access to critical information within their organizations. Identity and access management products offer role-based access control, which lets system administrators regulate access to systems or networks based on the roles of individual users within the enterprise. In this context, access is the ability of an individual user to perform a specific task, such as view, create or modify a file. Roles are defined according to job competency, authority and responsibility within the enterprise.
Some use cases for identity and access management include single sign-on systems, multi-factor authentication and access management. These technologies also provide the ability to securely store identity and profile data as well as data governance functions to ensure that only data that is necessary and relevant is shared. These products can be deployed on premises, provided by a third party vendor via a cloud-based subscription model or deployed in a hybrid cloud.
So where do you start?
The options to choose from are many, it is important to have an IAM strategy and an underlying process in place to enable the tool. Effective governance along with automated role management, authentication, user profiling and integration are keys to establishing a holistic IAM solution. An automated process that provides users with access to systems and revokes access when necessary forms the crux of IAM.
It is paramount to reach the right combination of confidentiality, integrity, and availability (CIA). Lack of periodic entitlement reviews and nonexistent links among human resources (HR) systems, active directory and enterprise applications result in inaccurate employee identification and employment status. These are two of the major reasons why IT security regularly comes up short in IAM strategies. Business process advancements fueled by technologies such as cloud, remote infrastructures, mobility and bring your own device (BYOD), along with changes in the way IT services are provided, such as multivendor outsourcing, Software as a Service (SaaS), multi-tenancy and virtual infrastructures, have made the IAM puzzle more interesting.
RealTek’s architects and IAM specialists will assist your organization in making the right decisions for your best security measures.
What should identity and access management include?
Identity access management systems should include all the necessary controls and tools to capture and record user login information, manage the enterprise database of user identities and manage the assignment and removal of access privileges. That means that systems used for IAM should provide a centralized directory service with oversight as well as visibility into all aspects of the company user base.
Technologies for identity access and management should simplify the user provisioning and account setup process. These systems should reduce the time it takes to complete these processes via a controlled workflow that decreases errors as well as the potential for abuse, while allowing automated account fulfillment. An identity and access management system should also allow administrators to instantly view and change access rights.
These systems also need to balance the speed and automation of their processes with the control that administrators need to monitor and modify access rights. Consequently, to manage access requests, the central directory needs an access rights system that automatically matches employee job titles, business unit identifiers and locations to their relevant privilege levels.
Benefits of identity and access management
IAM technologies can be used to initiate, capture, record and manage user identities and their related access permissions in an automated manner. This ensures that access privileges are granted according to one interpretation of policy and all individuals and services are properly authenticated, authorized and audited. Because companies that properly manage identities have greater control of user access, they’re able to reduce the risks of internal and external data breaches.
Automating IAM systems allows businesses to operate more efficiently by reducing the effort, time and money that would be required to manage access to their networks manually or via individual access controls that aren’t connected to centralized management systems. IAM systems help companies better comply with government regulations by allowing them to show that corporate information isn’t being misused. With identity and access management tools, companies can also demonstrate that any data needed for auditing can be made available on-demand.
Keeping the required flow of business data going while simultaneously managing its access has always required administrative attention. The business IT environment is ever evolving and the difficulties have only become greater with recent disruptive trends like; bring your own device, cloud computing, mobile apps, and an increasingly mobile workforce.
We have years of experience and believe that security in which ever form it may come in is paramount to ay organizations success. Our experts will ensure that we achieve the perfect balance of end-to-end security management for you needs.